阿帅
搜索
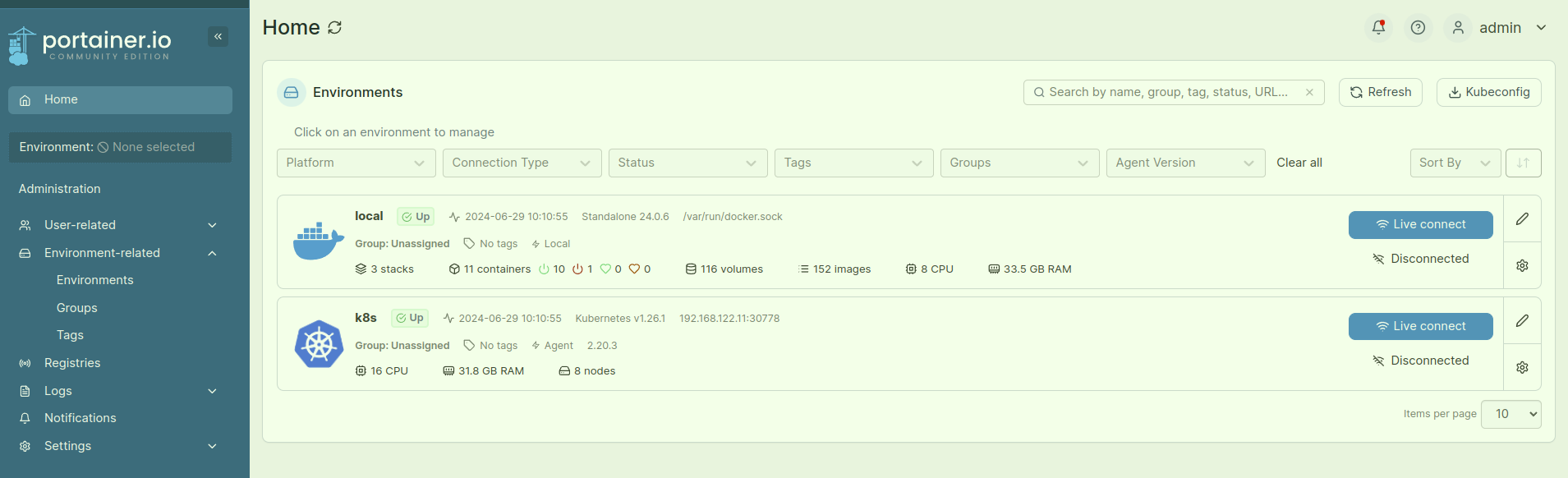
docker ui portainer
portainer
1 | docker compose -f portainer.yml |
portainer.yml
portainer.yml
version: '3.8' # 根据你的Docker Compose版本选择合适的版本号
services:
portainer:
image: portainer/portainer-ce:alpine-sts
container_name: portainer
ports:
- 8000:9000
- 9443:9443
extra_hosts:
- "portainer.ui.k8s.cn:192.168.122.1" # 添加主机名
volumes:
- /mnt/oss/portainer/data:/data
- /var/run/docker.sock:/var/run/docker.sock
- /mnt/oss/portainer/public:/public #chinese
chinese https://github.com/outlovecn/portainer-cn
docker pull m.daocloud.io/docker.io/portainer/portainer-ce:2.19.5
docker tag m.daocloud.io/docker.io/portainer/portainer-ce:2.19.5 portainer/portainer-ce:2.19.5
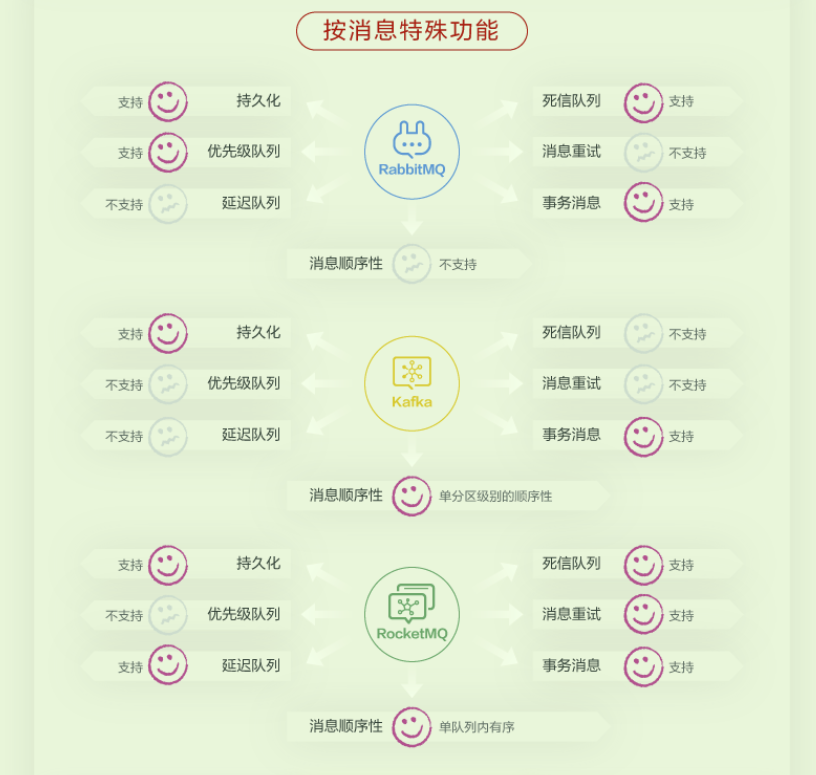
MQ 比较
差异
| 功能项 | RocketMQ | Kafka | RabbitMQ |
|---|---|---|---|
| 优先级队列 | 不支持 | 不支持 | 支持。建议优先级大小设置在0-10之间。 |
| 延迟队列 | 支持 | 不支持 | 不支持 |
| 死信队列 | 支持 | 不支持 | 支持 |
| 消息重试 | 支持 | 不支持 | 不支持 |
| 消费模式 | 支持客户端主动拉取和服务端推送两种方式 | 客户端主动拉取 | 支持客户端主动拉取以及服务端推送两种模式 |
| 广播消费 | 支持 | 支持 | 支持 |
| 消息回溯 | 支持 | 支持。Kafka支持按照offset和timestamp两种维度进行消息回溯。 | 不支持。RabbitMQ中消息一旦被确认消费就会被标记删除。 |
| 消息堆积 | 支持 | 支持。考虑吞吐因素,Kafka的堆积效率比RabbitMQ总体上要高。 | 支持 |
| 持久化 | 支持 | 支持 | 支持 |
| 消息追踪 | 支持 | 不支持 | 不支持 |
| 消息过滤 | 支持 | 支持 | 不支持,但可以自行封装。 |
| 多租户 | 支持 | 不支持 | 支持 |
| 多协议支持 | 兼容RocketMQ协议 | 只支持Kafka自定义协议。 | RabbitMQ基于AMQP协议实现,同时支持MQTT、STOMP等协议。 |
| 跨语言支持 | 支持多语言的客户端 | 采用Scala和Java编写,支持多种语言的客户端。 | 采用Erlang编写,支持多种语言的客户端。 |
| 流量控制 | 待规划 | 支持client和user级别,通过主动设置可将流控作用于生产者或消费者。 | RabbitMQ的流控基于Credit-Based算法,是内部被动触发的保护机制,作用于生产者层面。 |
| 消息顺序性 | 单队列(queue)内有序 | 支持单分区(partition)级别的顺序性。 | 不支持。需要单线程发送、单线程消费并且不采用延迟队列、优先级队列等一些高级功能整体配合,才能实现消息有序。 |
| 安全机制 | 支持SSL认证 | 支持SSL、SASL身份认证和读写权限控制。 | 支持SSL认证 |
| 事务性消息 | 支持 | 支持 | 支持 |
功能
http code了解
检查状态
集群
doc https://www.rabbitmq.com/docs/man/rabbitmqctl.8
1 | [root@rabbitmq-2 ~]# rabbitmqctl stop_app #停止节点 |
cluster_status
1 | rabbitmqctl cluster_status |
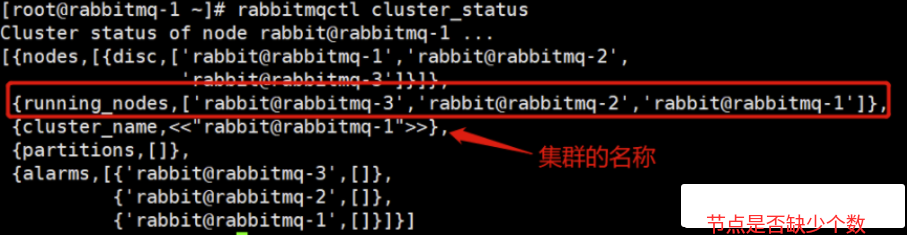
发生了网络分区
关注rabbitmqctl cluster_status字段 的partitions